Recording evidence gathered online
- Main
- Author's blog
- Recording evidence gathered online
Recording evidence gathered online
 544 views
544 views
A detective gathers the lion’s share of their evidence from open sources on the Internet. Despite the importance of this evidence, however, until now there have been no methodological recommendations for recording evidence found online. This state of affairs sometimes leads individual detectives to prepare a report just one or two pages long, under the mistaken impression that they are simplifying an evidence-recording procedure which is unnecessary.
We believe many providers of private investigative services would be interested to learn from our experience in gathering and recording evidence – after all, in 17 years of operations, not one of our reports has been disputed in a single court, in Russia or abroad.
In order for a detective’s report to stand up to scrutiny in court, it has to be compiled in a technically proficient manner and be free of errors and contradictions. Let’s take a closer look at what a ‘proper report’ should contain, and what information it should present in what format.
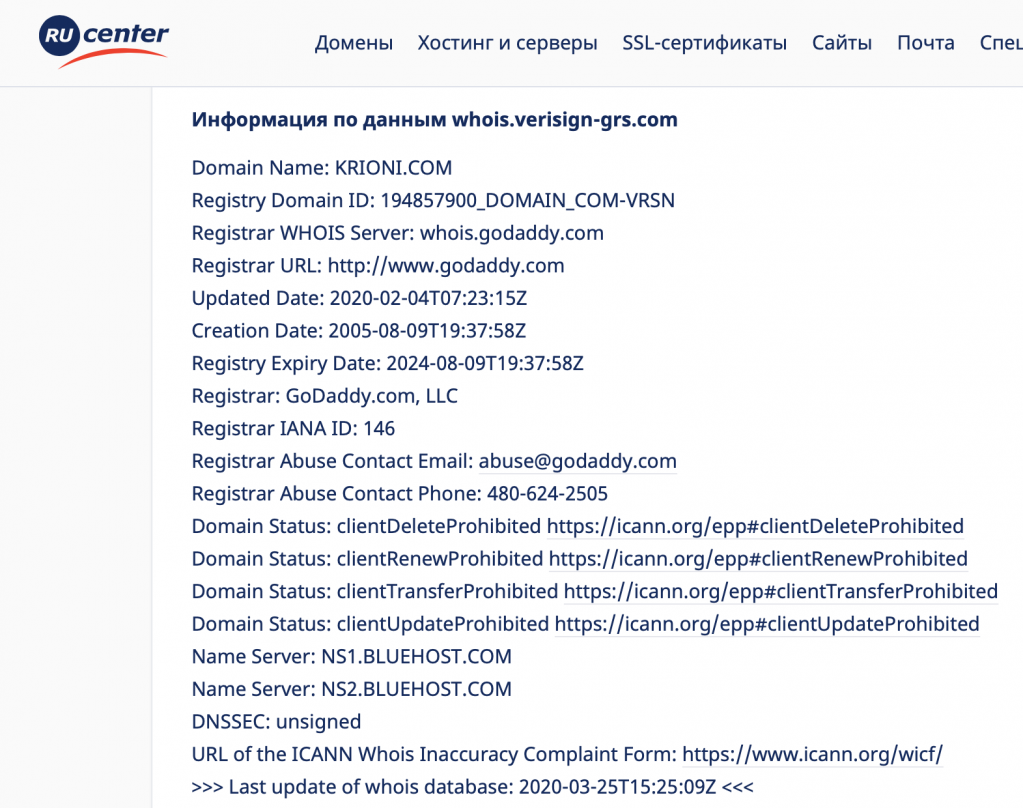
We will take the example of recording information a detective has obtained using the popular service Whois.
After turning on their computer and logging in, the detective launches their Internet browser. They then conduct a Whois search in relation to a domain name of interest to them where a particular webpage is located. After using appropriate software to take a screenshot, they then transfer the screenshot displaying the search result to a text editor (generally Word).
Every screenshot is accompanied by end-to-end numbering, the date and time of creation, and a list of equipment (brand and model of computer) and software used by the detective when examining and recording the evidence uncovered.
The list of software must include the name and version of the operating system, text editor, and all the software required to duly examine and properly record information. In some cases, the technology used to access the Internet is also listed: the router and the line used to access the Internet together with details of the provider (name and main state registration number of the network operator connecting the computer to the Internet).
Example:
|
|
Fig 1. Screenshot created on detective’s computer screen: iMac 21.5-inch, mid-2010, serial number W80517G1DAS, ATI Radeon HD 4670 256 MB graphics processor; system version: macOS 10.13.6 (17G11023), kernel version: Darwin 17.7.0, boot volume: Mac HD; on Thursday, 12 March 2020 at 11:54.
|
Finally, be aware that compiling a written report is a long and laborious undertaking which requires just as much effort and specialized technical knowledge as carrying out private investigative activities at an investigation site.
Detective Protocol
The Protocol is a process where two or more detectives interact with analytical tool ... [...]














